Operating in a world dominated by millions of malware-infected hosts acting as proxies for the facilitation of fraudulent and malicious activity, the Web’s most popular properties are constantly looking for ways to add additional layers of authentication to the account registration process of prospective users, in an attempt to undermine automatic account registration tactics. With CAPTCHA under automatic fire from newly emerging CAPTCHA solving/breaking services, re-positioning the concept from what was once the primary automatic account registration prevention mechanism, to just being a part of the ‘authentication mix’ these days, in recent years, a new (layered) authentication concept got the attention of the Web’s ‘most popular’. Namely, the introduction of SMS/Mobile number account verification, a direct result of wide adoption of mandatory prepaid SIM card registration internationally, in the context of preventing crime and terrorism.
Naturally, the bad guys quickly adapted to the new authentication mechanism, and in a true ‘malicious economies of scale’ fashion, undermined the concept, successfully continuing to populate any Web property with hundreds of thousands of bogus accounts, degrading the quality of the services offered, as well as directly abusing the one-to-one/one-to-many trust model in place. How do they do it? What type of tactics do they rely on in an attempt to bypass the mantatory prepaid SIM cards registration process, in order to secure a steady flow of tens of thousands of non-attributable SIM cards, at any given moment in time, empowering them to bypass the SMS/Mobile number activation account registration process? Let’s find out.
The practice, largely relying on the notion that, if a potential user would be required to present a valid ID to his/her mobile operator in order to get a SIM card, he/she would think twice before engaging in fraudulent, potentially malicious activities, in combination with limiting the number of SIM cards issued per person (for instance 10 prepaid SIM cards in Singapore, and 18 SIM cards per person in Vietnam), is sadly, fundamentally flawed due to a couple of reasons.
For years, the underground marketplace has been systematically supplying high-quality fake IDs/passports/diplomas/certificates and virtually any other kind of documentation, largely relying on a pool of talented designers, flawed secure printing supply chain logistics in terms of the easy to obtain blank plastics/document templates/holograms, as well as the actual equipment necessary to produce them in batches. This allows a cybercriminal/cybercriminal syndicate, to secure non-attributable access to virtually anything that requires a valid ID as means of authentication. That, ‘naturally’, includes compromised credit card details — sometimes required as an alternative to ID for the purpose of obtaining a SIM card — which in 2014, represents nothing more that a commoditized underground market item, largely due to the oversupply driven by the emergence of sophisticated crimeware releases, the evolution of ATM skimming technologies, and the bypassing of two-factor authentication/OTP, empowering novice cybercriminals with the necessary ‘know-how’ needed to obtain them. Yet another largely overlooked fraudulent tactic used to secure a decent supply of non-attributable SIM cards/mobile numbers, is the reliance on insiders, most commonly dealers of mobile operator services, monetizing the access to the operator’s databases, for fraudulent/malicious purposes.
Sadly, it wouldn’t be fraudulent/malicious operations in 2014 if they didn’t already manage to synchronize all levels of the fraudulent ecosystem, resulting in the commercial availability of APIs-supporting, 100% automated supply of non-attributable mobile numbers in a virtual, Web based environment, for the purpose of automatically bypassing the SMS/Mobile number activation authentication process of Russia’s most popular social networks, as well as the Facebook and Google account activation process. Which is exactly what the service that I’ll discuss in this post, is doing.
In addition to the 100% automation of the SMS/Mobile number activation process, thanks to a steady supply of non-attributable mobile numbers, and the fact that the service is guaranteeing that the number’s owner can never connect its use with that of the service’s core functionality, the service is also pitching itself as integration-ready with an extremely popular automatic account registration tool that specializes in bypassing the SMS/Mobile number account activation process.
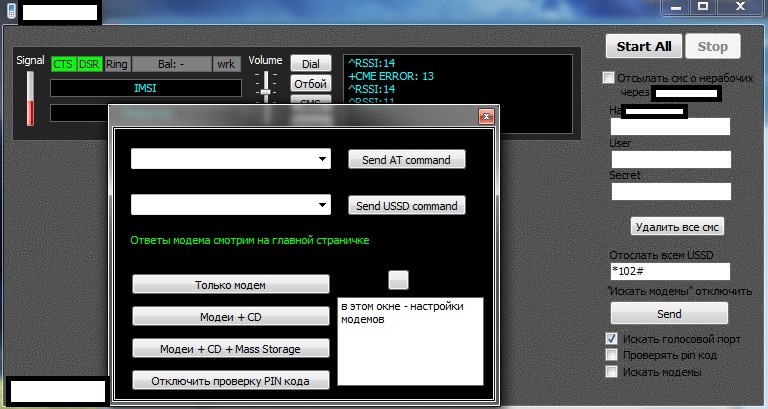
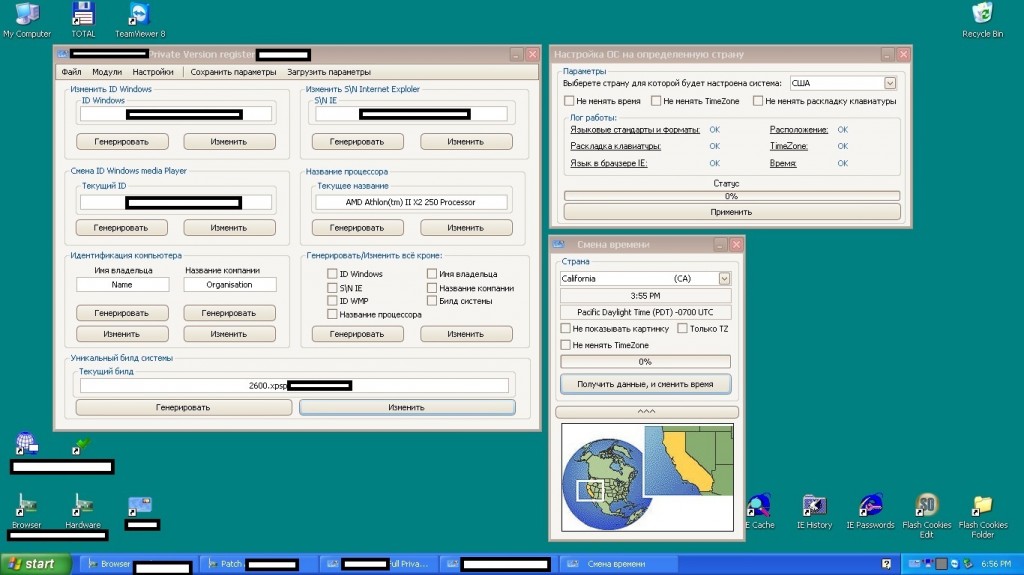
Sample screenshots of the customer’s panel showcasing the automatic SMS/Mobile number activation service’s core features:
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service]()
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service_01]()
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service_02]()
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service_03]()
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service_04]()
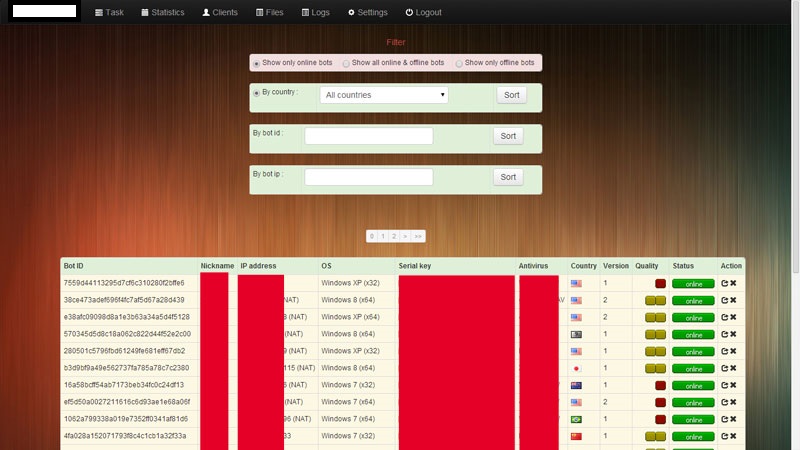
The service is already listing tens of thousands of available mobile numbers, to be abused in upcoming SMS/Mobile number account activation campaigns. Thanks to its API, it is also endorsing a DIY automatic account registration tool that’s exclusively specializing in SMS/Mobile number based type of registrations. The actual mobile numbers are Russia, Ukraine and Belarus “based”.
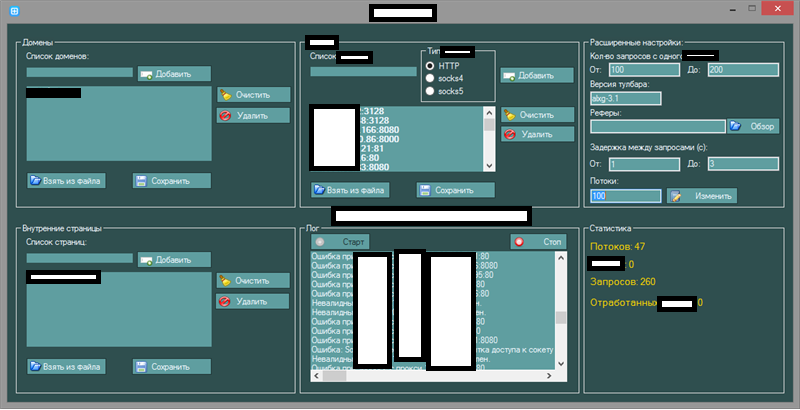
Sample screenshots of the automatic SMS/Mobile number account verification bypassing tool in action, exclusively relying on the service’s API:
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service_05]()
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service_06]()
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service_07]()
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service_08]()
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service_09]()
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service_10]()
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service_11]()
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service_12]()
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service_13]()
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service_15]()
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service_14]()
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service_16]()
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service_18]()
![SIM_Cards_SMS_Activation_Account_Registration_Bypass_Automatic_API_Service_17]()
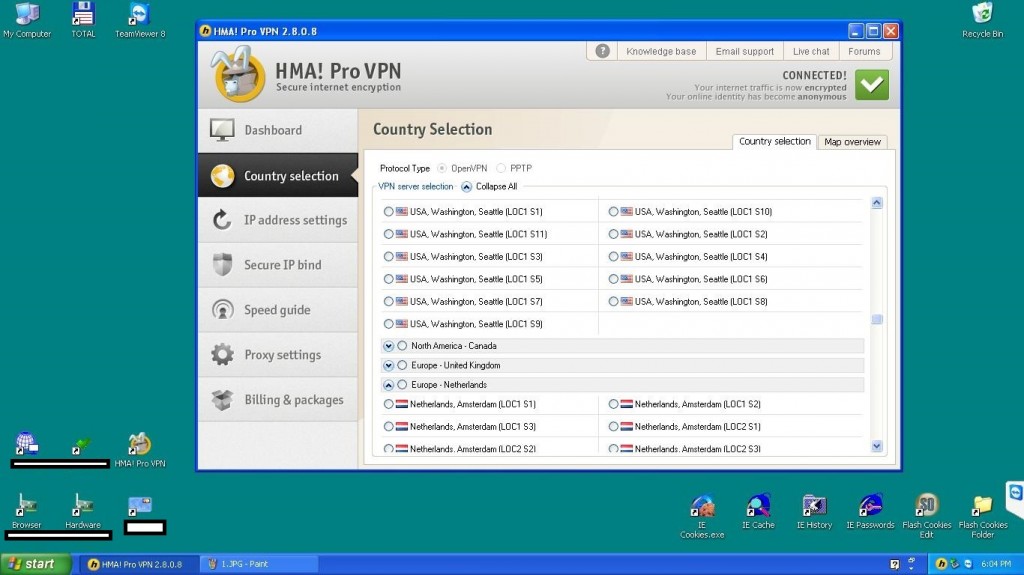
Another aspect of the fraudulent/malicious ecosystem behind the rise and commercially availability of this type of service, adapting to current automatic account registration protection mechanisms, is the reliance on insiders (dealers) of mobile operator services, for the purpose of supplying an endless stream of non-attributable mobile numbers. We’re currently aware of such insider activity, and we’re positive that a lot of similar activity is taking place under the radar.
Sample screenshot of the administration panel of a mobile service operator dealer’s admin account, showcased for the purpose of offering anonymous, on demand non-attributable mobile numbers, to assist in fraudulent/malicious activities:
![Anonymous_Phone_Numbers_Supply_Chain_Flaw_Insiders]()
As always, we’re actively monitoring this underground market segment, and will be posting updates, as soon as new developments take place.
The post Fully automated, API-supporting service, undermines Facebook and Google’s ‘SMS/Mobile number activation’ account registration process appeared first on Webroot Threat Blog.