Cybercriminals continue adapting to the exponential penetration of mobile devices through the systematic release of DIY (do-it-yourself) mobile number harvesting tools, successfully setting up the foundations for commercial managed/on demand mobile phone number harvesting services, ultimately leading to an influx of mobile malware/spam campaigns. In addition to boutique based DIY operations, sophisticated, ‘innovation’ and market development-oriented cybercriminals are actively working on the development of commercially available Android-based botnet generating tools, further fueling growth into the market segment.
In a series of blog posts, we’ve been profiling multiple cybercrime-friendly services/malicious Android-based underground market releases, further highlighting the professionalization of the market segment in terms of sophistication and QA (Quality Assurance).
We’ve recently spotted a service offering 5M+ harvested and segmented Russian mobile phone numbers on a per business status/gender/driving license basis. What’s particularly interesting about this service is the fact that it exposes a long-run fraudulent Win32:SMSSend serving infrastructure (SEVAHOST-AS Seva-Host Ltd (AS49313), segmented harvested mobile phone numbers of Sochi citizens, a fake (paid) medical leave/absence service targeting Sochi citizens, and a portfolio of rogue mobile apps leading to the exposure of a mobile botnet, surprisingly relying on an identical hardware/bot ID.
More details:
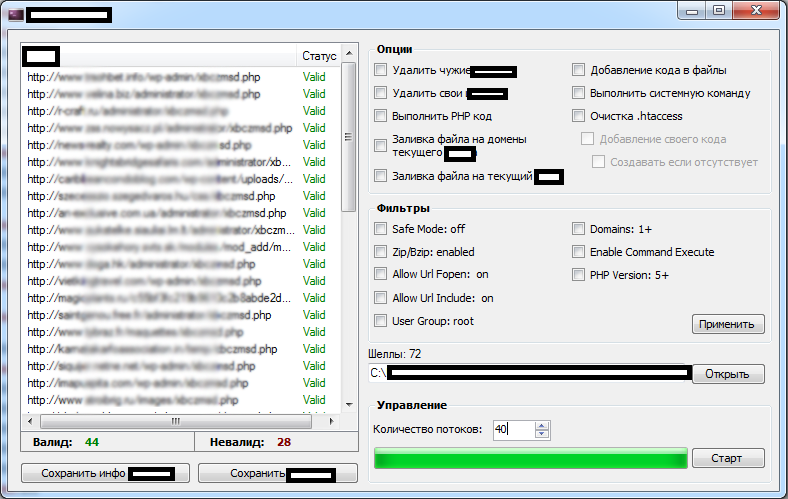
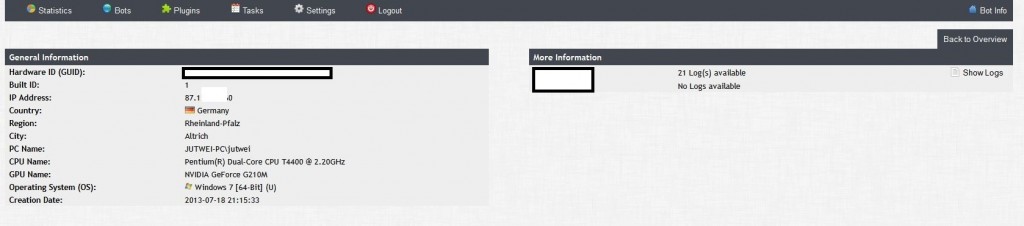
Sample screenshot of the 5M+ harvested mobile phone numbers service:
![Mobile_Malware_SMS_Spam_Fraud_Cybercrime_Harvested_Mobile_Phone_Numbers]()
The service’s main URL responds to 91.228.155.210.
Parked on the same IP (91.228.155.210) are also the following fraudulent/cybercrime-friendly domains:
hxxp://instagramm-registration.ru
Related rogue game MD5s known to have been (historically) hosted at the same IP (91.228.155.210):
MD5: 68c1c11d86bc272e9a975400e2991e41
MD5: 3ccf8cfc88d7228e8e4345d389ce56ef
MD5: 6bf0482a0bd8fcf19a88e7a03abd69ef
MD5: 232c501fec973e8923143e41b520f698
MD5: 5601f871f3f1873c1da971358799f088
MD5: 94abca6d4ec24fdbe1ec74f40b4a77cd
MD5: 126bc6cb8e58c7859768d9390c726774
MD5: 966e3bbd0f77463403bb200454544cd4
The following malicious MD5s are also known to have phoned back to the same IP (91.228.155.210):
MD5: 6e6a09ec8235705f314ed2fae8fab01a
MD5: 676dc0a061886bf537e01ddceb6c9230
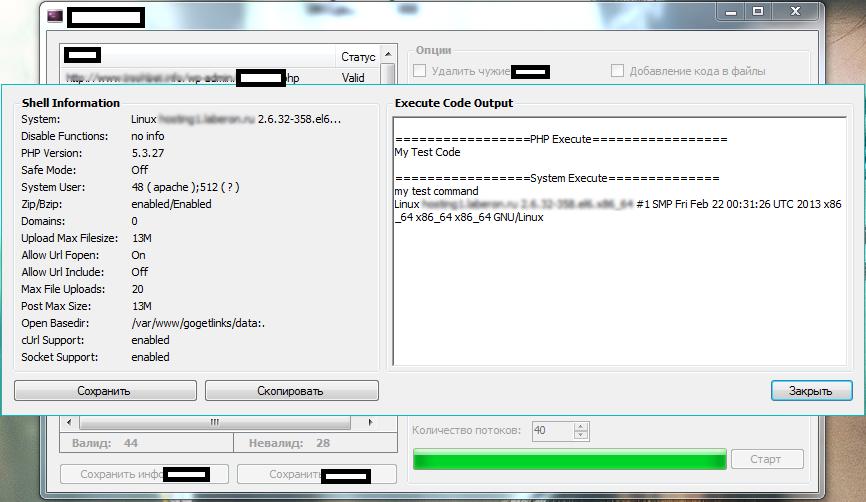
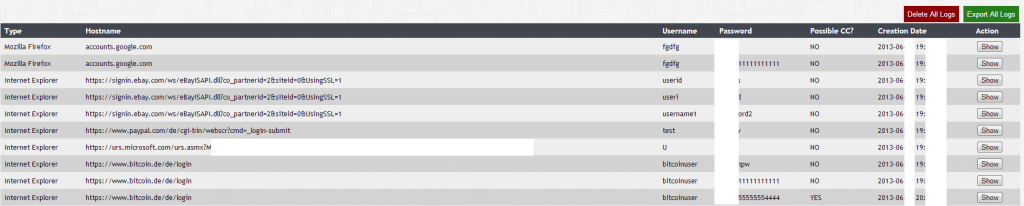
![Mobile_Malware_SMS_Spam_Fraud_Cybercrime_Harvested_Mobile_Phone_Numbers__]()
The existence of the secondary services (segmented mobile phone numbers belonging to Sochi citizens/paid medical leave services), parked on the same IP as the original 5M+ harvested mobile phone numbers offering service, is a decent example of market segmentation in the context of an event-based type of underground market offering targeting the Sochi Olympics. Not surprisingly, cybercriminals have already taken advantage of this segment, and in a true fraudulent/malicious nature, have launched social engineering driven Android-based malware serving SMS spam campaigns (MD5: 361e92c344294d8b4fce0c302f61716a).
![Mobile_Malware_SMS_Spam_Fraud_Cybercrime_Harvested_Mobile_Phone_Numbers__01]()
Sample screenshot of the fraudulent Instagram site parked on the same IP (91.228.155.210):
![Mobile_Malware_SMS_Spam_Fraud_Cybercrime_Harvested_Mobile_Phone_Numbers_01]()
Redirection chain for the rogue Instagram app site:
hxxp://instagramm-registration.ru/ -> hxxp://domainusers.biz/?page=lending&type=soft&size=1&ext=rar&link=http://tds-link-asg.biz/?tds=1275&page=search&parent=similar&key=Instagram_registration_(soft).zip&key=programma_instagram_register_PC ->
hxxps://www.tcsbank.ru/credit/form/cash/?utm_source=troywell_apr_cc&utm_medium=aft.apr&utm_content=network&utm_campaign=creditcard&wm=1otx&sid=701411425&prx=701411425
Redirectors domain name reconnaissance:
domainusers.biz – 91.202.63.117
tds-link-asg.biz – 91.202.63.119
![Mobile_Malware_SMS_Spam_Fraud_Cybercrime_Harvested_Mobile_Phone_Numbers_02]()
Name server reconnaissance for the redirectors:
NS11.LIMONBUCKS.COM – 91.217.85.34 – Email: sevacash@gmail.com – SEVAHOST-AS Seva-Host Ltd (AS49313)
NS12.LIMONBUCKS.COM – 91.217.85.37 – Email: sevacash@gmail.com
Name servers resonnaissance of the rogue/fraudulent mobile apps serving rogue affiliate network operating the redirectors:
ns1.sevadns.com – 91.217.85.35 – hxxp://sevadns.com -> hxxp://seva-hosting.com (91.217.85.35)
ns1.sevadns.com – 91.217.85.36
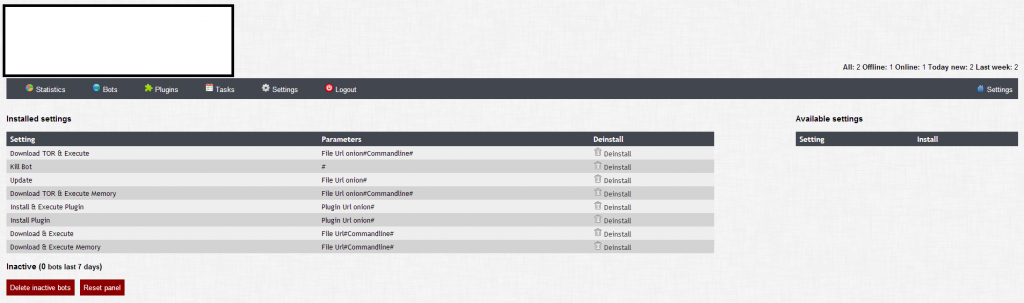
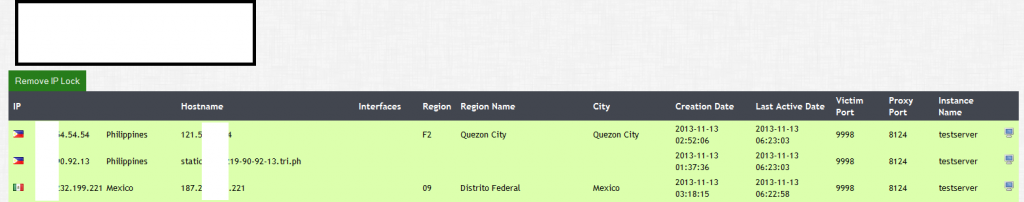
A peek inside sample statistics from the rogue mobile apps serving affiliate network:
![Mobile_Malware_SMS_Spam_Fraud_Cybercrime_Harvested_Mobile_Phone_Numbers_04]()
Known to have phoned back to (91.202.63.119; tds-link-asg.biz) is also the following malicious MD5: bf0074d6e2745925ec8ef3225a2052e1. Known C&C – hxxp://91.202.63.119/showthread.php?j6m=452416&nmhn=401c4ab9717ac07af8449176f3b07cfb&o=8,f4aacf34b635ccbe03dcc87bc52e7c49. Responding to the same IP, is also the Web site of the mobile traffic/rogue apps serving affiliate network.
Known C&C domain responding to the same IP: majdong.ru (91.202.63.119)
Related DNS requests performed by the sample (MD5: bf0074d6e2745925ec8ef3225a2052e1):
edreke.ru
edreke.ru.ovh.net
Name servers reconnaissance:
Name server: ns1.zippro.ru – 37.221.164.2
Name server: ns2.zippro.ru – 37.221.164.3
![Mobile_Malware_SMS_Spam_Fraud_Cybercrime_Harvested_Mobile_Phone_Numbers_03]()
Known to have phoned back to the same C&C server majdong.ru (91.202.63.119) are also the following malicious MD5s:
MD5: 9a05f7572ff50115fb22a4b3841ab137
MD5: 00adadb8e8a1d73c444134f2d1c1fba0
MD5: 651397e89d4b5687d1c8ce4834dc4234
MD5: bf0074d6e2745925ec8ef3225a2052e1
Known to have been downloaded from the same IP (ns1.zippro.ru – 37.221.164.2) are also the following malicious MD5s:
MD5: b58b0539818762becd4f5051a3c81b46
MD5: a385f6362f5ceb69db4c03ed324dfc34
Known to have phoned back to (ns1.zippro.ru – 37.221.164.2) are also the following malicious MD5s:
MD5: c6e5c1508ace1dfed450f8f69b11f1e6
MD5: f5399127b908f5a3ad994ca0e681cb26
MD5: aad3f6de5ae8c595797c55716a83adde
Known to have been downloaded from the same IP (ns2.zippro.ru – 37.221.164.3) are also the following malicious MD5s:
MD5: 522c729109ba4a51b5f361d33b5b3edb
MD5: 243934ec2546c54c1cb6d9309896a035
MD5: 578d5a1f5b968d01e553f7c94e12b235
MD5: b7baa6ccf6d9242b7e5d599830fa12b1
Known to have phoned back to (ns2.zippro.ru – 37.221.164.3) are also the following malicious MD5s:
MD5: ac3477ad87db7cfe4373cb2135eb1387
MD5: be49f224212ac9e05ae6b67b299350f2
MD5: a6f82de33bf03e8cb197cbc426942dca
MD5: 3204e633b6892171830004aedc5b6907
MD5: e31e8f4805768c326e28c68a6f406acc
MD5: d9920001704950e4f4c18d6e2ec30aae
MD5: 132cec7617f656db385d7acf31cd3393
MD5: be49f224212ac9e05ae6b67b299350f2
MD5: a6f82de33bf03e8cb197cbc426942dca
MD5: 93dfb678ecd06d27e59f96f2f30a52d5
Based on our analysis, we were able to successfully identify an identical pseudo-random hardware ID/bot ID, that we were also able to connect to related W32.SMSSend campaigns, further confirming that cybercriminals continue to actively multi-task in 2014.
Related W32.SMSSend hardware ID/bot ID campaigns using the same pseudo-random ID: 401c4ab9717ac07af8449176f3b07cfb
Sample fraudulent W32.SMSSend MD5s relying on the same pseudo-random ID known to have phoned back to 64.120.227.154/185.15.209.17:
MD5: ac3477ad87db7cfe4373cb2135eb1387
MD5: be49f224212ac9e05ae6b67b299350f2
MD5: a6f82de33bf03e8cb197cbc426942dca
MD5: 93dfb678ecd06d27e59f96f2f30a52d5
MD5: 3204e633b6892171830004aedc5b6907
MD5: e31e8f4805768c326e28c68a6f406acc
MD5: d6e06c98db7a0d38440d300accf8c730
MD5: d74528f426054fdcaca65a7e25b0d8dd
MD5: d1aa5e38fabe1811dfa113c6185c665e
MD5: 97141a85483998dff7e4aa04ce39b4f3
MD5: c6f2f67ddb2da9cebd9a669d964df6a7
MD5: 405b25f0834ad6c50ddfa203ac3112b4
Webroot SecureAnywhere users are proactively protected from these threats.
The post 5M+ harvested Russian mobile numbers service exposes fraudulent infrastructure appeared first on Webroot Threat Blog.