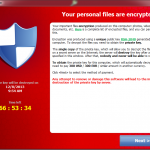
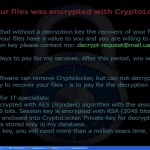
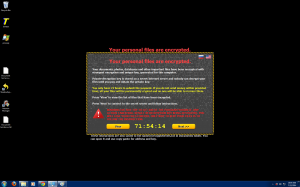
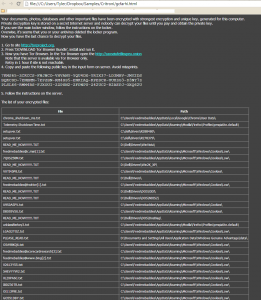
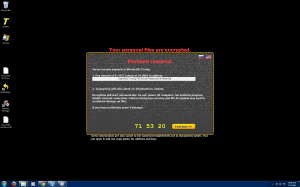
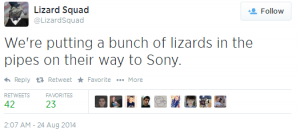
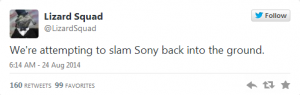
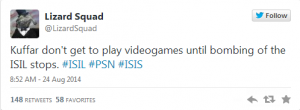
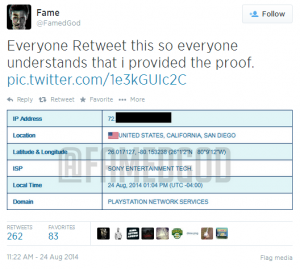
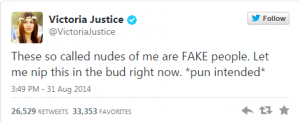
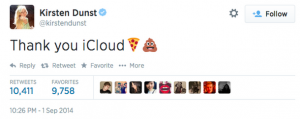
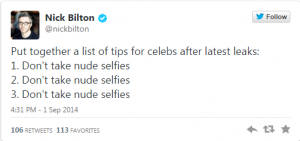
Well, September 9th is here, and the launch of Destiny, one of the most (if not the most) anticipated video games ever, isn’t the only major piece of news coming out of the tech world today.
You may have heard that one Cupertino fruit-logo’d tech company had an event today. And now the details of Apple’s next big(ger) things are official. Initial takeaway? They’re pretty in-line with the the rumors that have been swirling around for months now.
In other words, people got a lot of what they were expecting. Is that a good or bad thing? Depends on what camp you’re in. Probably.
Similar Phones, New Sizes
If you’re an Apple fan who’s only gripe was the small-by-today’s-smartphone-standards screen, your wish is (finally) Apple’s command. The company announced two new phones, each with a never before used (by Apple) size: the new iPhone 6 has a 4.7 inch screen while the new iPhone 6 Plus sports a 5.5 inch one. Yep, the iPhone will finally be competing in the phablet category.
![iPhone 6 and 6 Plus]()
(Source: ARS Technica)
The new devices are also thinner than the current 7.6 mm enclosure of the 5s, with the iPhone 6 measuring 6.9 mm and the iPhone 6 Plus coming in just slightly chubbier at 7.1 mm. To accompany these ‘gains’, Apple also introduces a new ‘Horizontal Mode’, which will help retain comfortable one-handed use and make everything within reach.
The glass now curves around the edges of the phones, but the screen isn’t the sapphire one many people expected, but rather incorporates “a slightly different design element”, according to CNET’s report. The phones’ power/lock button make a move from the top edge to the right spine.
The colors remain unchanged. You will be able to get the new devices in gold, silver, or space gray.
![iPhone 6 colors]()
(Source: PC Mag)
What about the display? The regular 6 gets a 1334×750 resolution with 326 PPI (Pixels Per Inch) while the 6 Plus gets a slightly crisper 1920×1080 resolution with 401 PPI. Both iPhones sport Apple’s familiar ‘Retina Display’ (although it’s now being called ‘Retina HD’). While these numbers improve on the 1136×640 (326 PPI) display of the 5s, they still lag behind many of today’s higher-end Android devices, a few of which (LG G3 and the newly-announced Galaxy Note 4 and Note Edge) pack 2560×1440 displays.
But pixels don’t always tell the whole story and it’s very difficult to tell the difference between 1080p and 1440p on such (relatively) small devices. That, and battery life typically suffers from a higher resolution. Speaking of…
The Internals
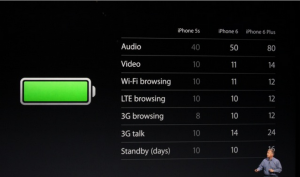
When it comes to battery life, Apple is claiming an improvement in battery life in both phones over the current 5s (see chart below)
![new iPhone battery life]()
(Source: ARS Technica)
The devices’ internal hardware gets a boost as well. The new iPhones are powered by Apple’s new A8 processor, which Apple says has 50% faster graphics and a 25% faster CPU. The transistor count has also been bumped up to 2 billion from the A7′s 1 billion. This should all lead to better efficiency and performance.
There’s also the M8 co-processor, which improves on the 5s’ co-processor and will assist the health-conscious iPhone users keep track of their activity and take better advantage of the iPhone’s fitness apps. It’ll also be handing the data coming from the new barometer sensor.
The phones also get upgraded LTE connectivity, bumping speeds up to 150Mbps. Wi-Fi speeds should also clock in at about three times faster than those of the 5s, thanks to Wi-Fi 802.11 support. VoLTE (Voice over LTE) and Wi-Fi calling are also now supported.
Camera
Updated rather than upgraded (if pixel count is your measurement), the camera in the iPhone 6 and iPhone 6 Plus retains its 8MP, but gets a new sensor with ‘Focus Pixels’ technology, which Apple claims uses DSLR-style phase detection autofocus, helping the new devices autofocus lock up to 2x faster than previous iPhones. Users will be able to record 30 and 60 FPS videos in 1080p and capture slow motion videos at 120 or 240 FPS, an improvement.
As far as image stabilization goes, the iPhone 6 gets digital stabilization, but you’ll have to purchase the bigger and more expensive (more on that later) 6 Plus if you want optical image stabilization.
If selfies are your thing, Apple also didn’t forget about its Face-Time camera (otherwise known as the front-facing camera), which receives a larger f/2.2 aperture plus a new sensor for better lighting and sharper image quality. Video capture remains at 720p and there’s also now a burst mode.
NFC/Apple Pay
![Apple Pay]()
(Source: Macworld)
Apple has resisted the NFC (Near Field Communication) push for years, but that no longer the case with the new iPhones. With the 6 and the 6 Plus, Apple not only added the protocol, but have also built their new Apple Pay payments system entirely for this cause. It works with the Passport app (as well as without it) and will finally allow users to use their new iPhone to purchase things. For more on Apple Pay, check out this Macworld article.
iOS 8
Apple announced that the new operating system will be available Wednesday, September 17th. For a detailed breakdown of the new features of iOS 8, check out this CNET article.
Pricing and Availability
The new iPhone 6 and 6 Plus will launch in eight countries on September 19th. Pre-orders begin on September 12th.
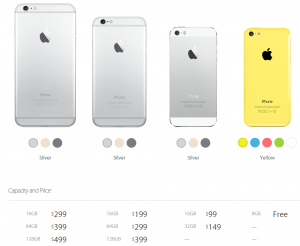
So far, Apple has only released US pricing, but, as you might expect, the new iPhones ain’t cheap. The iPhone 6 starts at $199 for the 16GB version. $299 will get you 64GB, and if you want the max 128 GB of storage, you’ll need to dish out $399. Tack on $100 across the board (for the same amount of storage) and voila, that’s how much the iPhone 6 plus will cost you. Yep, that means on-contract pricing for a 128 GB iPhone 6 Plus is a whopping $499!
In the US, the new iPhones will be available on AT&T, Verizon, T-mobile, Sprint, and US Cellular to start.
The other seven countries that get the September 19 launch are UK, Australia, Canada, France, Germany, Hong Kong, Japan, Puerto Rico, and Singapore.
This also means that the iPhone 5C’s price will drop to ‘Free’ and the iPhone 5S’s price goes down to $99 (for the 16 GB version).
![iPhone Prices]()
(Source: Apple.com)
‘One More Thing’: The Apple Watch
Apple didn’t end with the iPhone 6 and 6 Plus reveal, however. It wouldn’t be an Apple event if they did, would it? As many people expected, they introduced a new wearable device, called the Apple Watch (interestingly not iWatch like most predicted).
![iWatch]()
(Source: CNET)
The Verge has a very visual ‘hands-on’ write up and you can read it in its entirety here. Nevertheless, here’s some basic info on Apple’s long-rumored entry into the wearables market:
- Will be available ‘Early 2015′ starting at $349
- Will come in three collections – all different versions (with different finishes) of the same watch. The Apple Watch Edition will be finished in 18K gold.
- Touch-screen (flexible Retina) display, digital crown, infrared LEDs, and photo diodes
- Runs on an S1 Processor
- Equipped with gyro accelerometer
- Has NFC
- You need an iPhone 5 or better to use it
Security
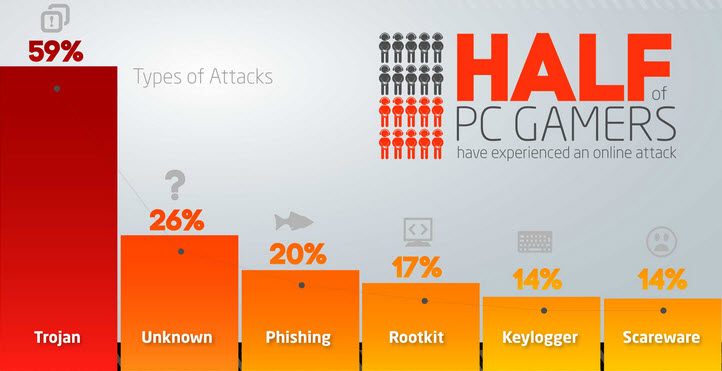
Many people forget that iPhones are not malware-proof. I won’t dive deep into this, but it’s important to keep your new devices protected, whether you’re an iPhone or Android user. We offer protection for both.
Concluding Thoughts
It will be interesting to see how consumers will react to the new iPhones. Many Android vs. Apple battles are already raging on in pretty much every comment section of every story written up on the iPhone 6 and 6 Plus.
The thing is, most Android and Apple users are already dedicated to their respective camps and I don’t think these new iPhones have enough revolutionary features that will lure many Android users away from their Google-powered machines, most of which already have the screen sizes Apple is finally embracing.
But because the 4.7 and 5.5 inch screens are a first for Apple, the real question comes down to the Apple fans themselves. Will the new screen sizes be the must-have addition many previous iPhone users were wishing for or will it alienate the fan base that loved Apple for offering a pocket-friendly premium smartphone?
For now, all we can do is wait and see.
The post Apple’s Sept 9 Event: New (and larger) iPhones and (gasp), a Watch! appeared first on Webroot Threat Blog.
 Webroot, the market leader in cloud-based, real-time Internet threat detection, recently returned from the 20th annual Gartner Security and Risk Management Summit in National Harbor, Maryland. Attended by many of the world’s top business and IT professionals in industries ranging from finance to information technology to government, the focus of this year’s conference was enablement of an organization to move forward towards its objectives, while ensuring security and protection. The show’s theme at this year’s conference, “Smart Risk: Balancing Security and Opportunity”, summarized the challenges that many large companies are experiencing today, as they work to ensure the safeguarding of their information without slowing down the company’s productivity.
Webroot, the market leader in cloud-based, real-time Internet threat detection, recently returned from the 20th annual Gartner Security and Risk Management Summit in National Harbor, Maryland. Attended by many of the world’s top business and IT professionals in industries ranging from finance to information technology to government, the focus of this year’s conference was enablement of an organization to move forward towards its objectives, while ensuring security and protection. The show’s theme at this year’s conference, “Smart Risk: Balancing Security and Opportunity”, summarized the challenges that many large companies are experiencing today, as they work to ensure the safeguarding of their information without slowing down the company’s productivity.