Nearly 50 percent of Americans don’t use antivirus software
That’s right; something as basic as installing internet security software (which we all know we’re supposed to use) is completely ignored by about half the US. You’d be amazed how common this and other risky online behaviors are. We did a survey of people’s internet habits across the United States, and the numbers aren’t pretty.
For reference, some very common (and very risky) online behaviors include:
- Not using antivirus software
- Sharing your account passwords
- Using too-simple passwords, or reusing the same password for multiple accounts
- Not using an ad or pop-up blocker
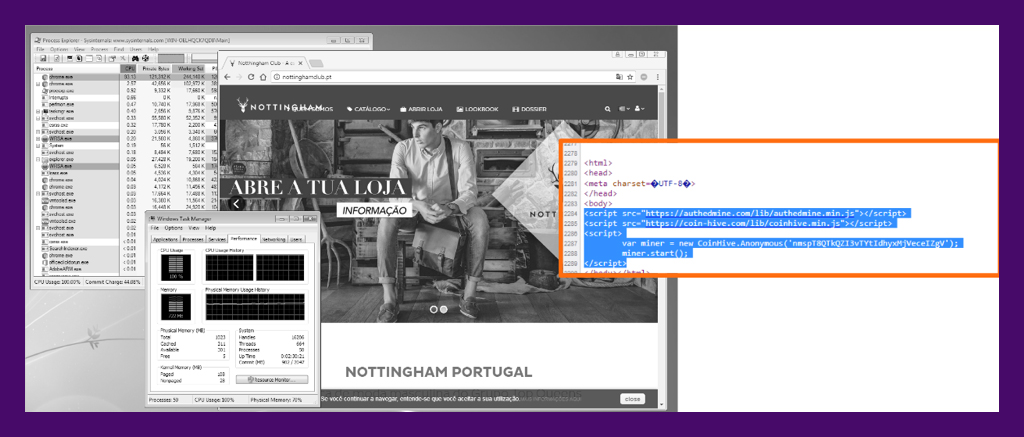
- Opening emails, clicking links, and downloading files from unknown sources
- Not installing security on mobile devices
State-by-state Breakdown of the Riskiest Cyber Behaviors
We analyzed all 50 states and Washington, D.C., to rank them on their cyber hygiene habits. This ranking system uses positive and negative survey questions weighted by the relative importance of each question. These questions address several topics, including infection incidents, identity theft, password habits, computer sharing, software update habits, antivirus/internet security usage, backup habits, understanding of phishing, etc.

Florida wins the dubious distinction of riskiest state with the worst cyber hygiene. But before anyone pokes fun, we’d like to point out that the average resident of any state in the nation has pretty poor cyber hygiene. Only 6 states in the nation had good cyber hygiene scores.
Impacts of Risky Behavior
When you engage practice poor cyber hygiene, you’re not just running the risk of getting infected or losing a few files.
In our research, we asked respondents who had suffered identity theft, “what were the main consequences of the identity theft incident?” Some of the self-reported fall-out was both surprising and tragic, including responses like divorced spouse, bankruptcy, failed to obtain mortgage, had to get second job, had to sell house, increased alcohol consumption, delayed retirement, and diminished physical health.
When we consider that identity theft can mean such devastating consequences as divorce, bankruptcy, and even damage to our health, it becomes clear just how important good cyber hygiene really is.
What the Riskiest States are Doing Wrong
Stats from the 5 riskiest states (Florida, Wyoming, Montana, New Mexico, and Illinois):
- Identity theft had little to no impact on their cyber hygiene habits. That means even after learning the consequences first hand, very few people changed their habits.
- These states had the highest per-person average (28 percent) of having experienced 10+ malware infections in a single year.
- 50 percent+ of respondents in Florida, Illinois, Montana, and 45 percent of respondents from New Mexico and Wyoming said they don’t use any kind of antivirus or internet security.
- 47 percent of respondents never back up their data.
- An average of 72 percent share their passwords.
What the Safest States are Doing Right
The 5 safest states had many behaviors in common that kept them ahead of the malware curve.
- Following cases of identity theft, nearly 80 percent of respondents from the 5 safest states reported that they had altered their online habits, and almost 60 percent changed their passwords.
- Only 14.4 percent of respondents the safe states experienced 10 or more infections a year.
- The safest states typically reported running paid-for antivirus/security solutions, rather than freeware, unlike their risky counterparts.
- Finally, nearly half (43 percent) of the 5 safest states automatically update their operating systems, and 35 percent of respondents regularly back up their data, either on a daily or continuous basis.
- And of the top 4, password sharing was hardly an issue (88 percent of respondents from those states reported they don’t share passwords at all.)
Find out which state your cyber hygiene puts you in. Take the survey below:
Please note that this survey is hosted by a third party, Typeform, SL. (“Typeform”). Your use of the Typeform survey platform will be subject to their Terms and Conditions. Any information you provide in answering the survey questions will be anonymized so that it cannot be used to identify you.
The Role of Demographics and additional findings
Given Florida’s reputation as a retirement hotspot, we wanted to point out that 50 percent of Florida’s respondents in our study were age 30 or below, and the national average of respondents aged 30 or below was 47 percent. This means age demographics in our survey were consistent throughout all 50 states and D.C. and our responses actually skew younger rather than older.
How to Increase Your Personal Cyber Hygiene Score (It’s not too late!)
Here’s a quick to-do list that will help keep you safe from malware, identity theft, and other online risks. It’s not as hard as you might think.
- Use antivirus software. And keep in mind, while there are plenty of free tools out there that are better than nothing, you get what you pay for. Your online security, and that of your family, is worth a little investment.
- Create strong passwords for each account, change them often, make sure each one is unique, and, if possible, add spaces for increased security. If you’re worried about keeping track of them all, use a password manager.
- Stop sharing your login credentials with friends, family, and coworkers. We mean it.
- Closely monitor your financial accounts for any fraudulent activity, and consider using a credit monitoring or identity protection service.
- Regularly update your operating system and software applications. Lots of infections start by exploiting out-of-date systems.
- Don’t open emails from people you don’t know, and don’t download anything from an email unless you’re certain it’s legitimate. And if you get a message that appears to be from an official or financial institution asking you to take an action, don’t click any links. Go straight to the institution’s official website, or call them to confirm whether the message you received was real.
- Back up your files and important data regularly to a secure cloud or physical drive.
There are a lot of risks out there, and as an internet user, you have a responsibility to use good judgement when you work, bank, shop, browse, and take other actions online. But by following these easy tips, you can dramatically change your cyber hygiene score, and reduce your risk of falling victim to cybercrime.
The post American Cybercrime: The Riskiest States in 2018 appeared first on Webroot Blog.